Why Choose Us?
Outstanding customer experience is a direct result
98%
Open rate
60%
Read within
5 min
10x
Better engagement
than email
20+
Years in the business

Improve Customer Engagement using our Powerful Text Message Marketing Software
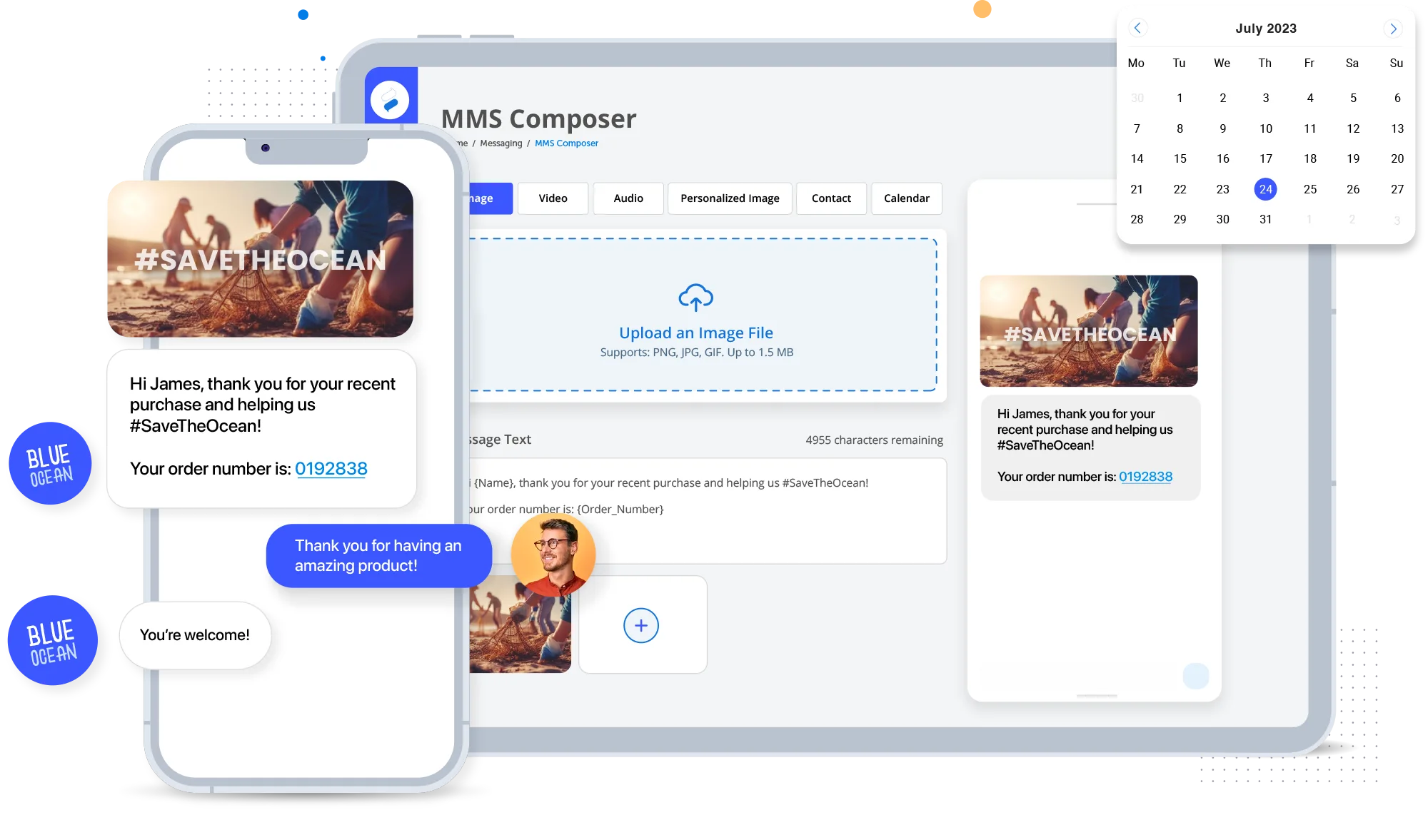
Engage with customers by sending them text messages containing pictures, video, text, hyperlinks, animated gifs, contacts, calendars, and more.

Send SMS Notifications to Customers & Employees with our Service Messaging Platform
Send service related messages to customers and employees. Service messages can be scheduled ahead of time or sent automatically through APIs.
Integrations
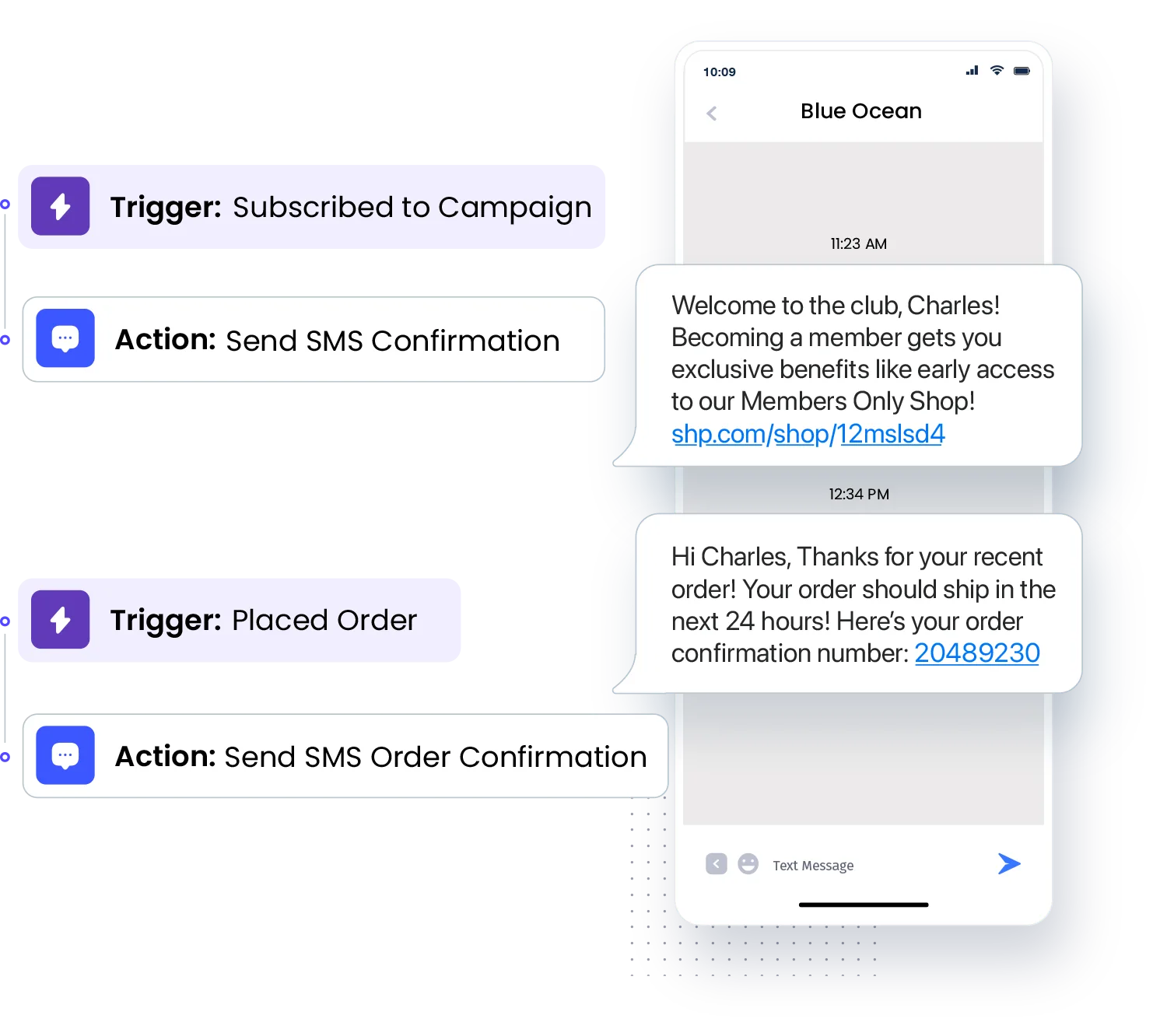
Automate the Conversation with our Text Messaging API
SMS API
Our SMS API enables businesses to trigger text messages automatically. Use our SMS API to send a standard text message that may contain personalized information, such as the recipient’s name.
MMS API
Our MMS API enables businesses to trigger picture or video messages automatically. Use our MMS API to send personalized pictures, videos, gifs, and more.